Within the space of a week we had yet another unusual case to investigate thanks to ACSIA monitoring our systems regularly and notifying us in real time of anomalies and irregularities targeting our server infrastructure.
Now lets walk through this particular case in a little detail.
ACSIA notified the event as an XSS attack, even though it did not succeed, it aroused my curiosity and I decided to look into this case.
Below is the snippet captured from the logs where everything started:
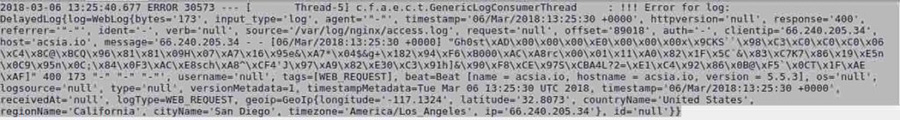
The attack originated from IP 66.240.205.34 and the attacker under the name “Gh0st” tried to inject a malicious script via XSS attack technique with the intention to compromise the servers and extract data from them.
Therefore we go on ACSIA’s dashboard and query to populate all activities related to this IP address.

Below is the screenshot with our findings:
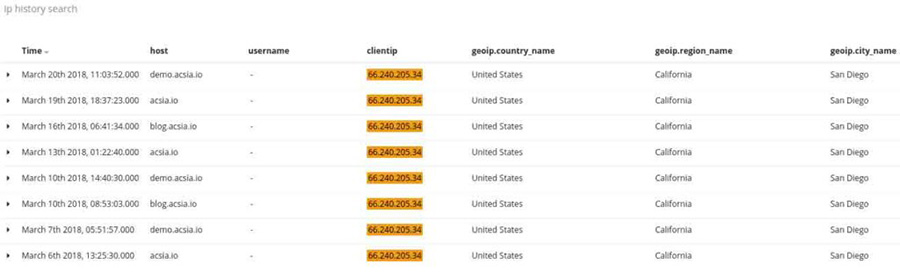
As we can see from the full list and activity of that specific IP address, the attacker attempted to maliciously access our main web server, blog and demo web site.
We can expand in detail one of the attacks:
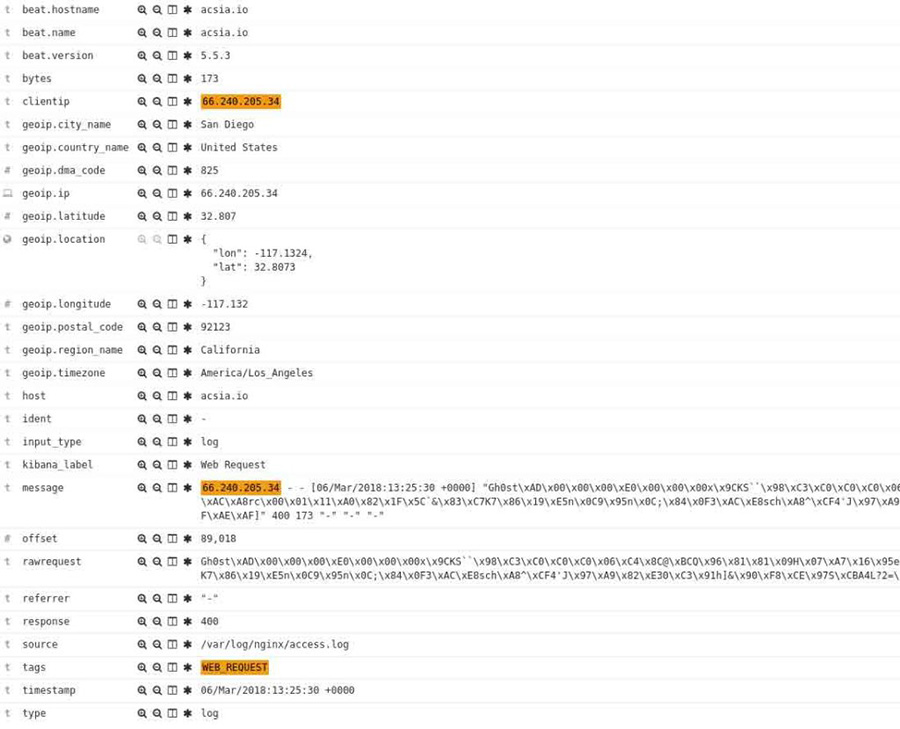
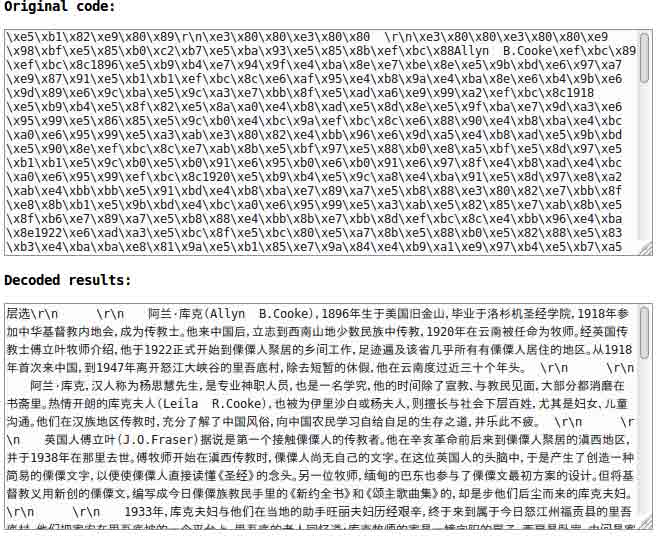
A typical XSS attack with the intent of trying to inject malicious code. We then try to decode the malicious code:
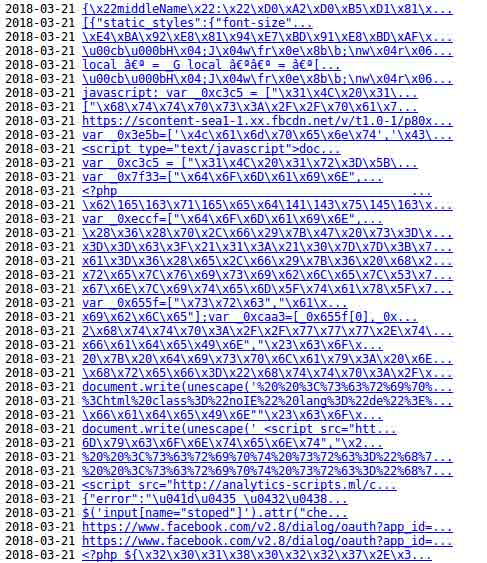
The decoded result seems to be some sort of Chinese characters but further decoding the result, the snippet below reveals this as a database query that embodied with some other website such as ancestry.com .
I am not going to dig further here as it is clear enough to me that we are confronted by an XSS attack that apparently copies database queries executed <and maybe succeeded> on other websites including ancestry.com and so on.

From the above decoding, one of the query seems to be originating from ancestry.com:
Lets go back to the attacker’s IP address which is 66.240.205.34 and get some details about it.
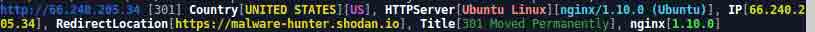
First thing we do we run some network scanner to check if either is a webserver or something else.
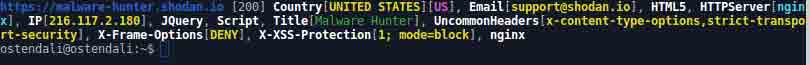
And there we are, it is a web server Ubuntu Linux installed with nginx web-server and it resolves to https://malware-hunt.shodan.io/ .
That is really interesting…
We just follow the link and click on it.

It is the popular search engine for IoT as per the article advertised on The Hacker News: https://thehackernews.com/2017/05/shodan-malware-hunter.html
In the beginning I said that this was another unusual case because this one is a sort of dilemma. The reason behind this attack seems to be hunting for malware. At least this is what they say publicly on the website which we are going to reveal shortly.
This really is a dilemma because I couldn’t figure out why someone would attack with malicious intent, performing an XSS (Cross-Site-Scripting – https://en.wikipedia.org/wiki/Cross-site_scripting) attack with the simple intention to check if my system either has been affected by malware.
The dilemma deepens because:
- I didn’t ask for such analysis
- I did not authorize this assessment (this is a deeply invasive assessment, normally organizations need to provide express written permission for such).
- I don’t think the attacker is an internet NGO or charity organisation trying to help me out
- Who the heck are these people??
So it appears that Shodan Malware project is going around the internet and performing unauthorized malware detection scans on 3rd party servers.
What can I say, very ambitious people and I wonder what next they are going to do.
To initiate a mass DDOS attack to everyone in the search of malware?
We obviously will report the case to them upon publication of this article.
Happy Hacking!!!
