With all the excitement of our first Release Candidate launch last week, it’s nice to step back and get some feedback from our system. We have deployed ACSIA to monitor a number of our internal monitoring systems while we continue development and improvement – after checking in on our system left running over the weekend, we had a chance to see ACSIA in action in the real world, notifying and protecting our systems.
We have left the monitoring and alert notifications running for the weekend. We have received about ~243 notifications from one of our servers.
Some of emails listed below in the screenshot…

The interesting thing is that out of the 243 notifications, 242 were originating from the same IP address. This IP address has made several mass-scan attacks against our product’s website which we happen to have set up just a few days before we launched ACSIA.
This IP “24.173.98.42” succeeded in getting our attention and we just wanted to have a quick look into who this might be and what else it has attempted on our servers. ACSIA will provide us all we need to achieve this 🙂
So here is one of the email notification we have received so far from ACSIA:

As we can see from the above notification, this type of attack is trying to find if we happen to have a tool called pypmyadmin2018 on our server and so on.
Now, let’s take a closer look at what ACSIA can provide us to investigate this case.
We filter our “Live Notifications” by the IP address and here are a few of their attacks listed in the below screenshot:
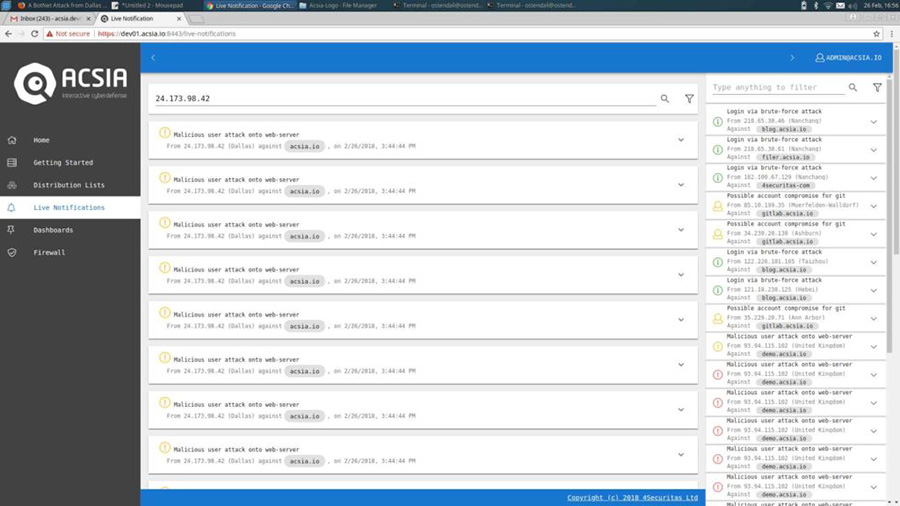
We click on an individual notification and get its details; e.g. the IP’s geographical location and the type of attack, as per below snippet:

Among other options, ACSIA has IP tracking, which will take us onto a dedicated dashboard where we can see all traffic related to this IP address.
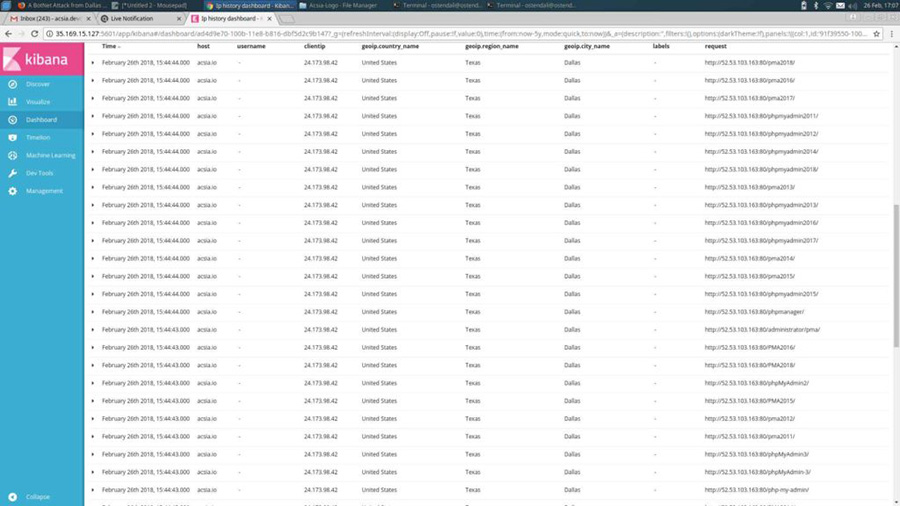
In the above screenshot we can see the list of all of malicious requests made by that IP address.
We go further and pick one of the malicious requests to be analysed in detail. The snippet below show the details “Mozilla/5.0 muhstik-scan” is the type of attack:

ACSIA has been very efficient in notifying all of this in real time, and it ascertained that our product website integrity has not been compromised; that the attack was ended without achieving anything relevant that would represent a threat.
The WhoIs record for this IP address, as shown by ACSIA, shows us that this IP is owned by a company called Time Warner Cable Internet LLC:

Before we proceed to ban this IP permanently, we would like to do some further investigation purely out of curiosity – this is one of the main issues troubling hackers, isn’t it 🙂
So let’s dig in and have a look who this would-be intruder is…
We just run some deep “nmap” scanning against the IP address:

Nmap scan indicates that this device is appear to be Dell SonicWall Security appliance:

Usually these sort of appliances have web interfaces and we just wanted to confirm this:
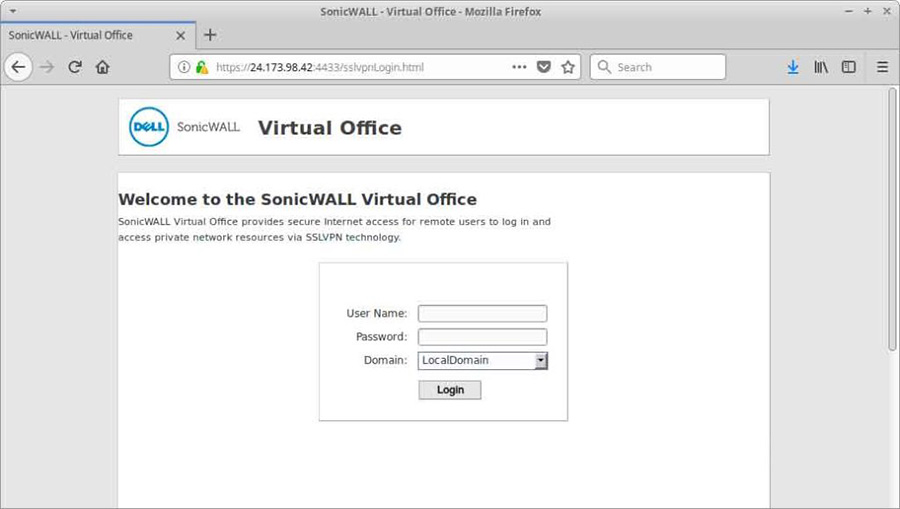
And we have the confirmation of course.
Let’s do some further digging to get more details from this device:

And there you go – the system has some vulnerabilities….
We have established that the device behind the Dell SonicWall Network Security Appliance is actually a PC running Windows 10.
So we are dealing with a script kiddie here, who is running Kali Linux in a VM, and using several automated mass-scan tools to attack an entire subnet. Our server happens to be part of that subnet 🙂
Happy Hacking!!!
Disclaimer: some personal information about the attacker has been withheld in order to protect their identity.
